Changing specific from Windows to Mac users for the Phishing plan
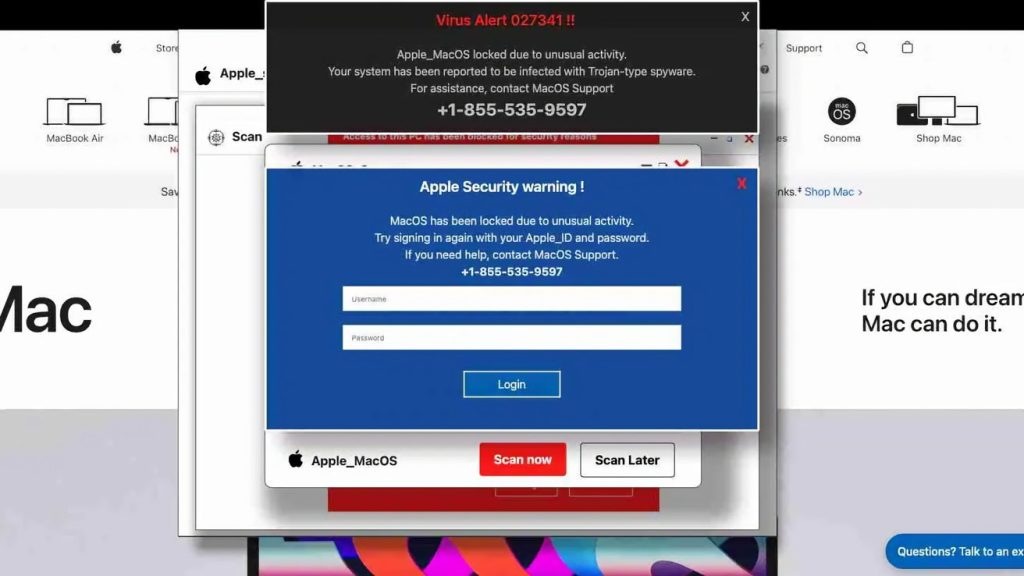
A site that targets Mac people is being targeted by hacking attacks. Image Credit: LayerX Labs
A fresh phishing scheme targeting Mac users has been discovered, one that changed its tactics after the recently targeted Windows users received an update to the Edge website. Phishing attacks are a prevalent threat to victims of cybercrime, with online criminals setting up websites and sending out messages deceiving users into providing sensitive information. Although the practice of using fake websites or emails may target almost anyone, there are times when the target audience can change for unanticipated reasons. &# 13, One more attack discovered by security firm LayerX Labs has been found to specifically target Mac users. Although the move’s most recent targets use mac, the phishing campaign really had a different target group at the beginning. It was originally targeted at Windows people. The 13th, Great phish campaign, which was detailed on March 19 by LayerX, was a powerful one that appeared to be false security updates within Windows. The attack, which was monitored for more than a year, used compromised websites to show the false instructions, which claimed the Computer was” compromised” and “locked” A glass appeared that asked users to enter their Windows username and password. The website that users actually loaded up was frozen and nonfunctional as a result of the use of harmful code, giving the impression of a locked display. The battle was hosted on Microsoft’s Windows, which further strengthens the trustworthiness. Users are led to believe the communications were actually from Microsoft themselves on a net software meant to host Cloud applications. It was a challenging campaign to stop, especially because some of the page’s infrastructure was used by safe web gateways and message security tools, and it was difficult to do so for various reasons as well. Additionally, the attackers relied on random and rapidly changing domains, which allowed the strategy to continue even when some subdomains were flagged as destructive. The victim attempted to access a legitimate website, but unintentionally there was a common mistake in the URL. &# 13, The strike worked. They would be directed to a damaged area parking page, which then directs the user through a number of websites before attempting to reach the targeted phishing attack page. &# 13, LayerX described the websites and pictures used to deceive people as well as being well-designed and specialized in nature. Additionally, automated tools that may identify phishing campaigns were used, such as Captcha and anti-bot identification systems. By late 2024 and first 2025, LayerX discovered that the battle was getting more and more intense, but it wasn’t the only one to notice it. Microsoft itself witnessed the assault, and it blocked it by adding a fresh “anti-scareware” element to the Edge computer. &# 13, At the same time, Google Chrome and Mozilla Firefox both received similar defensive features, which in turn helped reduce the number of problems. 13, After their advantages, LayerX saw a significant reduction in Windows user attacks. It wasn’t entirely gone; malicious websites were also active, but it was unable to show the bogus warnings to users. The attackers decided to concentrate their efforts and equipment on a different target group: Mac users, with Windows users no longer a viable target as a result of the computer updates. &# 13, Just two weeks after Microsoft released its Edge changes, LayerX began to see the same problems being carried out against Mac users. Prior to the changes being made, the business hadn’t noticed Mac-related assaults. &# 13, Adapted attackA new attack targeted Mac users, according to LayerX, making Safari customers the main objective. &# 13, But, the attackers kept many of the information the same and just changed a few details in order to avoid wasting the already-deployed infrastructure. For instance, the communication and structure of phishing pages have been updated to fit more with macOS apps. &# 13, The code was also updated to use HTTP OS and user agent parameters to filter out potential victims on MacOS. Strangely, despite the effort to adjust, the campaign remained dependent on Windows. .net network &# 13, LayerX asserts that the existence of the Mac version demonstrates that criminals are willing to modify while security firms work to get up and stop this hacking plan. There were surprisingly some significant changes when attempting to attack Windows users. It even demonstrates that Mac and Safari people are a prime target for phishing attacks by online thieves. &# 13, Secure yourselfUsers usually have great online hygiene to prevent phishing attacks. It can be obvious that something is wrong to check for basic greetings in messages, crazy provides and promises, and typographical errors in URLs and images. &# 13; In the event of a browser-based attack like the one above that claims a computer has frozen, a frozen tab can typically be closed or forced to quit completely if the warning is a fake. Additionally, it’s unlikely for Apple to ever really warn Mac users about threats coming from any kind of Windows area. Some users should be able to avoid the virtual traps by taking a moment to consider warnings and other odd messages that demand payment information or credentials.
 rumored to distribute to the bottom iPhone 17 yet another Motion screen
rumored to distribute to the bottom iPhone 17 yet another Motion screen  Apple Watch might acquire cameras for physical intelligence
Apple Watch might acquire cameras for physical intelligence  An all-plastic Apple Watch SE may be something Apple might be thinking about.
An all-plastic Apple Watch SE may be something Apple might be thinking about.  Unleaked phone Flip leaker confirms forecasts for 2026 launch.
Unleaked phone Flip leaker confirms forecasts for 2026 launch.  Unintentionally, the Philips Hue Secure door leaks from an iOS app
Unintentionally, the Philips Hue Secure door leaks from an iOS app  Criminal vial: A teen criminal of an Apple Store agrees to pay security personnel.
Criminal vial: A teen criminal of an Apple Store agrees to pay security personnel.